Threat Intelligence
HOW IT WORKS.
Threat intelligence involves gathering and analysing information about emerging or existing threat actors and their tactics, techniques, and procedures (TTPs). This knowledge enables organizations to anticipate potential attacks and strengthen their defences accordingly, disrupting the early stages of the kill chain by preventing attackers from successfully finding vulnerabilities and delivering their malware.

HOW PROAXIOM DOES IT
Cyber Threat Intelligence is central to our other service offerings. The Cyber Threat Intelligence (CTI) lifecycle is a structured process Proaxiom uses to provide tailored intelligence services. It includes:
Direction : Establishing the intelligence requirements based on customer-specific needs, known as Priority Intelligence Requirements (PIRs). PIRs determine what intelligence is relevant to the customer, such as specific threat actors or vulnerabilities that could impact their industry or technologies they use.
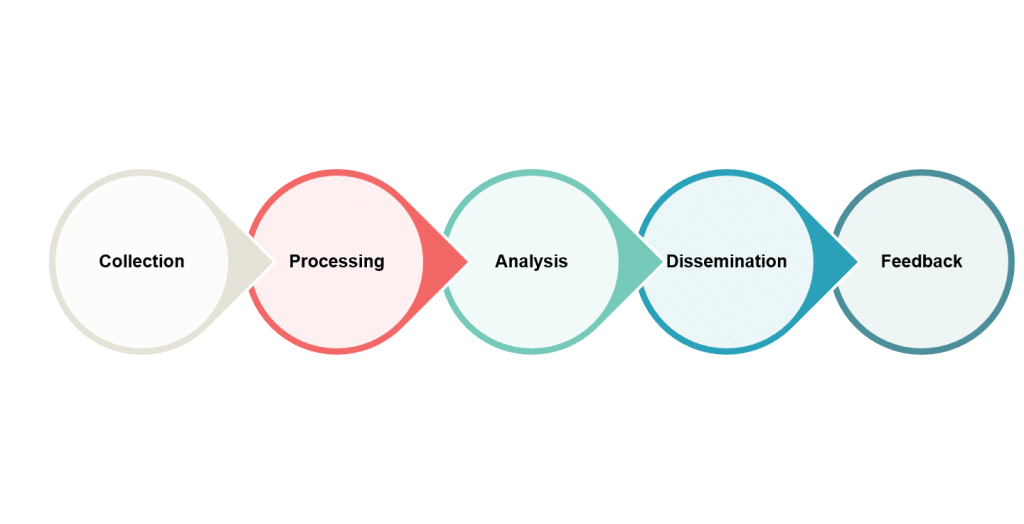
Collection : Gathering data from a combination of high-quality commercial sources and Open Source Intelligence (OSINT). This diverse range of sources ensures a broad spectrum of information, from dark web intelligence to public domain information.
Processing : Converting the collected data into a format suitable for analysis. This includes sorting, categorizing, and preparing the data for detailed evaluation.
Analysis : Examining the processed data to identify patterns and deduce the tactics, techniques, and procedures of threat actors. This analysis is informed by the customer’s PIRs to ensure it is relevant and actionable.
Dissemination : Distributing the actionable intelligence to the customer. This involves integrating the intelligence into the customer’s security infrastructure for improved detection and enforcement, as well as correlating with the SIEM as threat indicators.
Feedback : Receiving input from the customer on the intelligence provided. This feedback loop refines the direction phase, ensuring that the intelligence remains aligned with the customer’s evolving requirements.
In addition to these phases, customized threat intelligence is used to prioritize vulnerability management. By understanding which threat actors are pertinent to the customer and what exploits they typically use, Proaxiom can help prioritize patching the vulnerabilities most likely to be targeted.
Furthermore, this intelligence feeds into proactive security measures, such as threat hunting. By identifying likely targets within the customer’s environment, Proaxiom can search for signs of compromise or attack that have evaded standard detection mechanisms, thereby enhancing overall security posture.
HOW DO WE REPORT?
We provide a monthly threat intelligence report that details the threat intelligence we’ve collected that matches our customers priority intelligence requirements, where it was collected from, how we processed it, the output of our analysis and how the threat intelligence was disseminated to detection and enforcement systems.
How would this mitigate a threat actor like a Blackcat ALPHV affiliate?
RECONNAISSANCE
Proaxiom receives credible threat intelligence from a dark web monitoring service that a Blackcat ALPHV affiliate, identified as UNC4466, is targeting organisations in the same industry vertical as the customer. We provide advance warning to the customer of the threat actor’s known operations. The threat intelligence includes dark web chatter that mentions our customers asset information, including IP ranges, domains, user names, accounts and other network identifiers. Proaxiom reviews threat intelligence for TTPs and IoCs and extends coverage where gaps exist. As an example, dark web chatter may reference a compromised account – Proaxiom would revoke sessions on this account and force self-service password reset.
WEAPONISATION
The threat intelligence also contains details regarding the weapons used in UNC4466’s current campaign, including file hashes for the malware used as the encryptor. Proaxiom implements security controls to block the execution of the malware and to issue an alert if it is detected in the network.
Delivery
The threat intelligence includes details about UNC4466’s delivery methods for this campaign. These include advanced social engineering techniques such as impersonating IT support. Proaxiom constructs an awareness training bulletin and provides it to our customers staff for internal distribution. Users awareness is heightened to the threat and subsequent social engineering attempts have a lower probability of succeeding.