WHAT WE DO
Within just 8 weeks our Audit to Assurance + Cyber Insurance Readiness program enables SMBs
to achieve Essential Eight Maturity Level 3 compliance. With embedded cyber insurance policy parameters, our integrated software provides Audit to Assurance + cyber insurance readiness. All of this underpinned by a Managed 24*7*365 Security service to keep your business protected from Day 1.
ACCESSIBLE

AFFORDABLE

AROUND THE CLOCK
AUDIT TO ASSURANCE
ESSENTIAL
EIGHT
COMPLIANCE
INSURANCE
READINESS
24*7*365
SOC
AUDIT TO ASSURANCE PROGRAM.
Compliance Framework Assessment
Cyber Insurance Assessment
Sovereign Managed Security
Proaxiom empowers Australian businesses to reduce cybersecurity risk by guiding them through the selection and implementation of suitable cybersecurity frameworks, such as ASD Essential Eight, NIST CSF 2.0, SOC2, and ISO 27001.
Our comprehensive “Audit to Assurance” program ensures a seamless process, beginning with framework selection and roadmap creation, followed by assisting clients in achieving compliance. We also evaluate readiness for cyber risk insurance and facilitate compliance with insurance requirements.
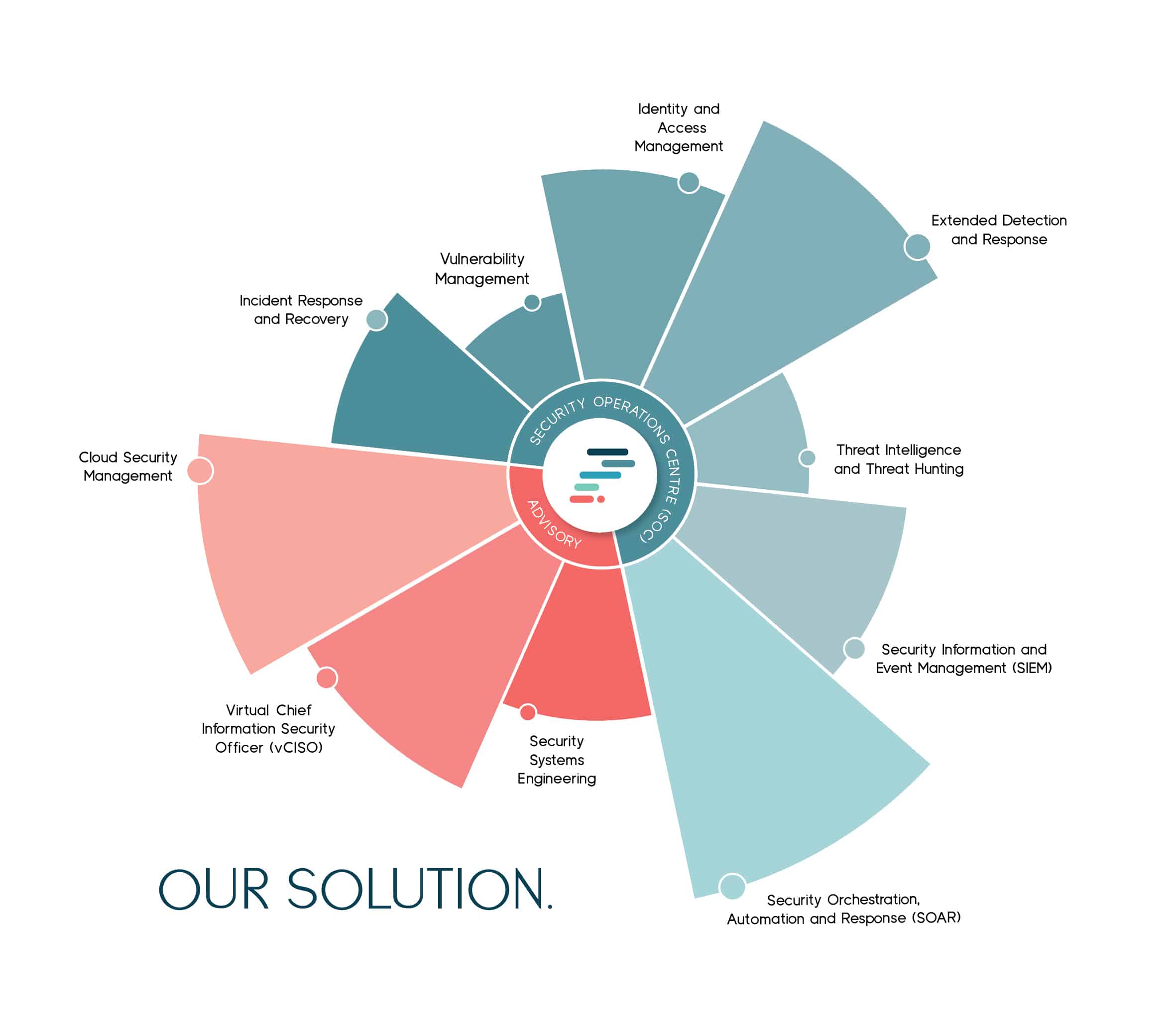
Our managed security services provide ongoing support for framework compliance, encompassing asset management, detection and response, incident response, vulnerability management, and threat hunting.
CYBER
PROTECTION
FROM
DAY 1

With our inclusive approach to cybersecurity solutions you
can rest easy knowing that every angle is covered, your assets secured,
your risk managed and your business protected around the clock with
24*7*365 mitigation and remediation support through a dedicated Security
Operations Centre (SOC).
ESSENTIAL
EIGHT READINESS.
The Essential Eight framework is a cybersecurity initiative
developed by the Australian Cyber Security Centre (ACSC). The
framework is used by organisations across Australia and New
Zealand to set the standard for cyber protection and is a strong
base from which to satisfy:
STAKEHOLDERS
Knowing their assets and investments are protected through
24*7*365 coverage
CUSTOMERS
Providing diligent oversight and control of their data meeting
Australian standards
STAFF
Reducing exposure to risk through embedded endpoint
protection and oversight
INSURERS
Controlling premiums by meeting the Australian industry
benchmark


ABOUT THE ESSENTIAL EIGHT
The Essential Eight framework consists of eight essential mitigation strategies that are considered fundamental in preventing
and mitigating targeted cyber intrusions.
These strategies are:
- APPLICATION CONTROLS
Allowing only approved and trusted applications to run on
systems, to prevent the execution of malicious software.
- PATCHING APPLICATIONS
Regularly applying security patches and updates to fix
vulnerabilities in applications, including operating systems,
web browsers and other software.
- CONFIGURING MICROSOFT OFFICE MACRO SETTINGS
Disabling or limiting the use of Microsoft Office macros, often
used as a vector for malware delivery.
- USER APPLICATION HARDENING
Configuring web browsers and other user applications to
minimise the risk of exploitation.
- RESTRICTING ADMINISTRATIVE PRIVILEGES
Limiting access to active and essential users to reduce the
potential impact of a compromised account.
- PATCHING OPERATING SYSTEMS
Regularly applying security patches and updates to address
vulnerabilities.
- MULTI-FACTOR AUTHENTICATION (MFA)
Providing an additional layer of security to access controlled
systems and resources.
- DAILY BACKUPS
Regularly backing up critical data and systems to ensure
they can be restored in the event of a compromise or failure.

INSURANCE READINESS.
We keep track of developments in the cybersecurity insurance industry, undertaking extensive research into defining and interpreting emerging trends and requirements from cybersecurity insurers.
To help SMBs tackle this minefield of requirements, we’ve embedded an Insurance Assessment framework within our Essential Eight Audit Assessment. This ensures you’re compliant and meeting the industry standards from the Australian Signals Directorate (ASD) – and for your insurers.
By understanding the parameters needed for both, our comprehensive audit ensures your business is protected and your cyber posture assured for insurers too.


24*7*365
SOC.
We find our customers appreciate the importance of a Security Operations Centre (SOC) to their business, however the cost and time investment needed to find and retain security talent, select, negotiate, purchase and integrate the various systems and implement threat monitoring and management 24*7*365 is an impossible business case to justify in-house.
Our Audit to Assurance program already includes Managed Security to provide around the clock cyber talent and technologies monitoring cyber threats from the moment our services are activated, at a fraction of the cost of establishing that same assurance capability in-house.
While technology is a critical part of every cybersecurity offering, people are at the heart of everything we do. So, we’ve put together an elite team of cybersecurity experts structured around the Security Operations Centre Capability Maturity Model (SOC-CMM).
- A top-tier analyst, oversees the entire team and strategy.
- A dedicated security operations architect is responsible for the overall architecture of the SOC.
- Our service desk, aligned to the ITIL framework, supports service delivery by managing service
requests and incidents and keeping our customers informed about our response activities
TIER ONE
ANALYSTS
for initial
investigation
TIER TWO
ANALYSTS
for deeper
threat analysis
and response
TIER THREE
ANALYSTS
for advanced
threat hunting
and major
incident
response
