Incident Recovery
HOW IT WORKS.
Incident response services kick in after an attack has been detected or suspected that can’t be managed through the standard detection and response process. Specialists work to quickly assess the scope of the breach, contain the threat, eradicate the attackers’ presence, and recover affected systems. By efficiently managing the aftermath of an attack, these services prevent further damage and restore normal operations, disrupting the attackers’ ability to complete their mission.

HOW PROAXIOM DOES IT
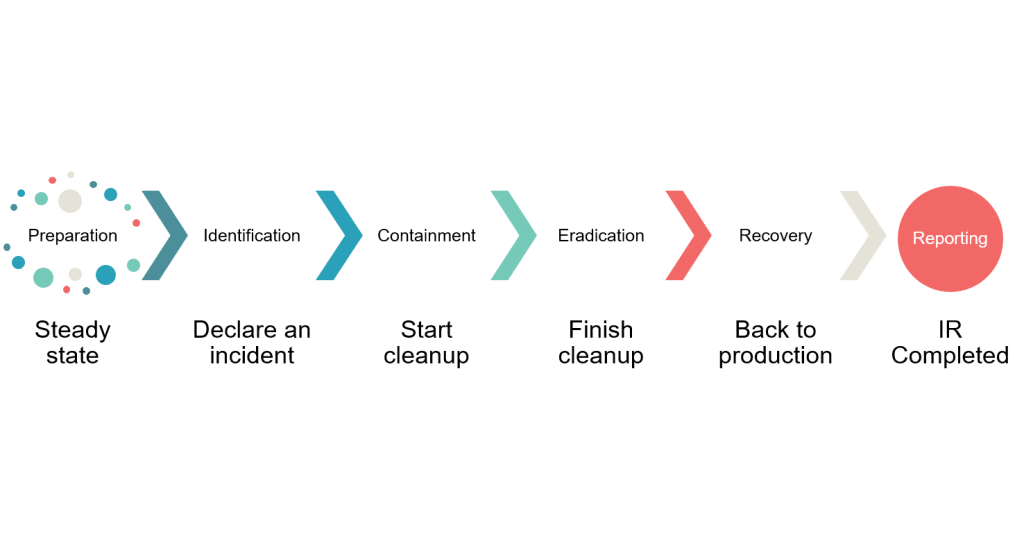
When an incident occurs that cannot be addressed through the standard detection and response mechanisms, Proaxiom escalates to its incident response process. This process is activated for incidents that either defy containment and eradication efforts or are of such severity that they demand a more concentrated approach.
Proaxiom’s Incident Response process aligns with the industry-standard SANS Institute’s Incident Response steps. This structured approach ensures comprehensive threat mitigation and recovery, tailored to safeguard customer environments against cybersecurity threats.
Dissemination :
Proaxiom establishes robust incident response capabilities during the initial customer onboarding phase, which are continuously improved over time as part of the managed service. This phase includes setting up the necessary infrastructure and tools for detection and response, such as firewalls, SASE platforms, identity platforms, XDR/EDR systems, and network sensors. Additionally, it involves training the response team and briefing clients on the process. Notably, the preparation and identification phases are conducted without drawing down on the incident response retainer.
2. Identification
Proaxiom employs advanced telemetry from security infrastructure, aggregated in the Microsoft Sentinel SIEM, to detect behaviors that match known Tactics, Techniques, and Procedures (TTPs) of threat actors. Alerts generated are carefully triaged to differentiate between false positives and true incidents. Upon positive identification of an incident that cannot be resolved through the standard detection and response process, Proaxiom initiates the incident response process. This marks the point at which the incident response retainer begins to be utilized. A war-room conference with customer stakeholders and any other relevant parties is convened to ensure effective communication and coordination throughout the incident response. The incident response process may also be invoked due to the severity or scope of the incident.
3. Containment
The containment phase aims to limit the scope and impact of the incident. Proaxiom’s approach includes immediate containment actions as predefined measures within their standard detection and response protocol. For incidents requiring escalation, Proaxiom employs additional, specialized containment strategies to prevent further spread or damage.
4. Eradication
Following containment, Proaxiom focuses on thoroughly removing the threat from the environment. This may involve deleting malicious files, revoking unauthorized access, and applying necessary patches. Proaxiom leverages its extensive resources and, if required, collaborates with external incident response teams to ensure complete eradication of the threat.
5. Recovery
In the recovery phase, Proaxiom orchestrates the restoration of affected systems and services to full functionality, ensuring they are cleared of any threat remnants. This includes careful validation of system integrity and close monitoring for any signs of persistent threats or vulnerabilities.
6. Lessons Learned
After the incident is resolved, Proaxiom conducts an in-depth review to extract valuable lessons from the incident. This comprehensive analysis results in a detailed report that covers the incident’s timeline, the effectiveness of the response actions taken, and recommendations for preventing similar incidents or improving the response in the future.
It’s important to note that the incident response process is iterative. During regular “steady state” operation, we’ll move between preparation (managing telemetry) and identification phases (managing alerting based on IoCs and TTPs).
During an incident, we may detect other threat actor activities during the recovery phase and may be required to jump back to the containment phase as a result.
Recognizing the limits of its own capacity, Proaxiom maintains relationships with external incident response teams for additional support including Division 5 and Triskele Labs, ensuring readiness for incidents even if we’re oversubscribed.
HOW DO WE REPORT?
We deliver an after-action report at the closure of every incident.
How would this mitigate a threat actor like a Blackcat ALPHV affiliate?
ACTION ON OBJECTIVES – INCIDENT RESPONSE
In the Blackcat ALPHV affiliate example, Proaxiom might detect action on objectives by detecting Tor traffic when the affiliate issues the ransom or communicates with a user. We may also detect indicators of compromise that are known to be used by Blackcat ALPHV affiliates.
Our incident response team launches a war room to keep our customer up to date with situation reports. We block data exfiltration using the CASB solution based on the indicators we identify during investigation. We use the SIEM to trace back the threat actor’s actions to different systems that the attack was launched from. We contain these machines by isolating them using the EDR and then identify the C2 framework that remained undetected. We contain and eradicate the C2 framework and block the threat actor’s indicators. We invoke the process for restoring data from offsite backup and return service to normal. We write a post-incident report, including lessons learned. We gather any threat intelligence we can gather during the incident, and share it back to the ASD using the CTIS platform.

