Detection and Response
HOW IT WORKS.
Detection and response services continuously monitor and analyse the network and endpoint activities to identify malicious behaviour or anomalies that indicate a cyber-attack. Once a threat is detected, rapid response measures are initiated to contain and mitigate the threat, thus preventing the attacker from achieving their objectives.

HOW DOES PROAXIOM DO IT?
We follow the industry standard approach to detection and response, with specific methodologies that ensure comprehensive protection and swift action against potential threats.
Our approach begins with the integration of cutting-edge technology and robust processes tailored to meet the unique needs of each client. We employ a multi-layered security strategy that encompasses a variety of advanced tools and techniques to identify and mitigate risks effectively.
We emphasise continuous improvement through regular assessments and updates. By conducting periodic security audits and staying abreast of the latest cybersecurity advancements, that your defenses are always robust and the risk of cybersecurity compromise is appropriately managed.
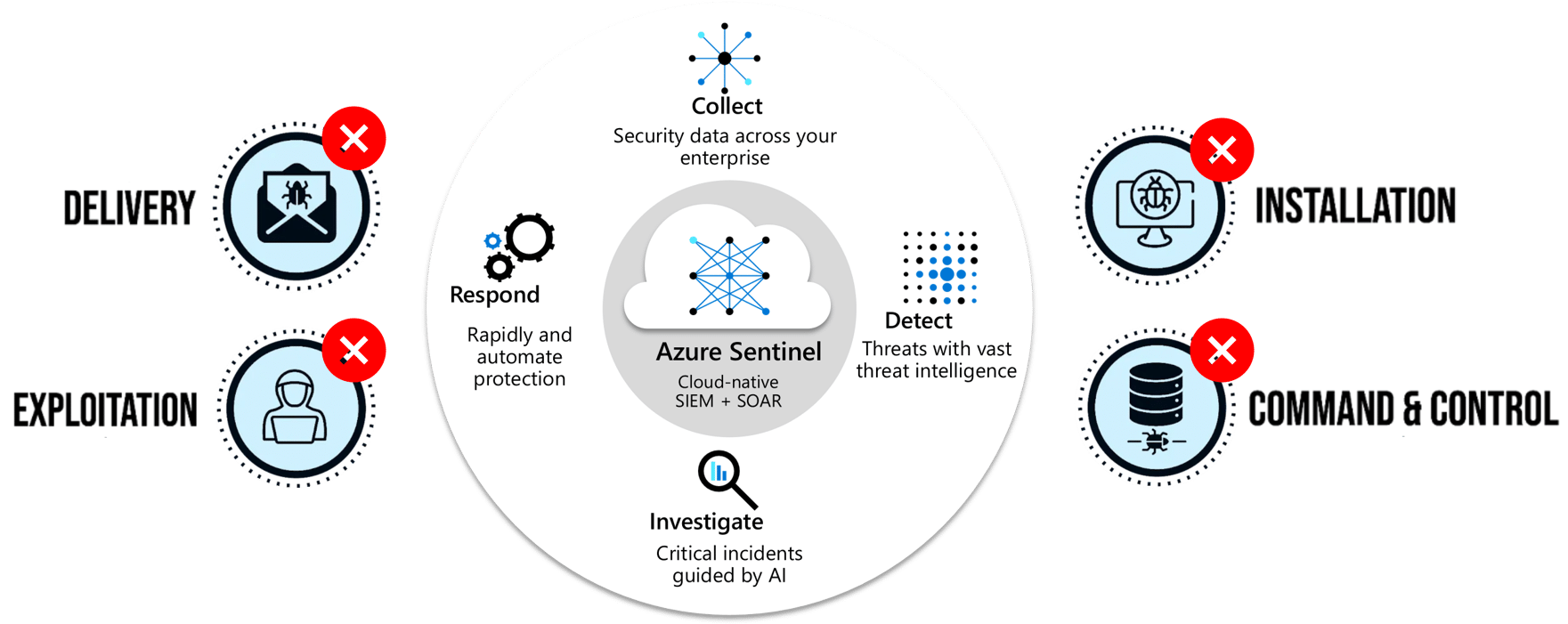
COLLECT: Through data connectors and integrations, Microsoft Sentinel combines data from all Microsoft and non-Microsoft sources, including users, devices, end point applications, infrastructure environment, and third-party data to understand the full digital estate. We configure and integrate advanced security infrastructure within client environments to serve as both detection mechanisms and enforcement points. This infrastructure encompasses a wide range of tools, including but not limited to firewalls (e.g., pfSense), Secure Access Service Edge (SASE) platforms (e.g., Cloudflare for Teams), identity management platforms (e.g., Microsoft Entra ID and Active Directory), Extended Detection and Response (XDR) and Endpoint Detection and Response (EDR) systems (e.g., Microsoft Defender XDR), and network sensors (e.g., Zeek).
DETECT : The telemetry data collected from these sources is aggregated in a Security Information and Event Management (SIEM) platform, specifically using Microsoft Sentinel, a cloud-native SIEM solution. Proaxiom customises Sentinel to detect specific behaviors indicative of known threat actors, referred to as Tactics, Techniques, and Procedures (TTPs), using Threat Intelligence to ensure accuracy and relevance to current threats, and to ensure we have adequate coverage of TTPs, introducing new detection logic in response to known threat actor activity.
Built-in artificial intelligence and machine learning uses Microsoft’s analytics and threat intelligence to detect previously uncovered threats. It analyses signals from different data sources, reducing noise from alerts, minimising false positives, drilling, and analysing anomalous events to present incidents that really require attention.
INVESTIGATE : Alerts generated through these detection mechanisms are meticulously triaged to distinguish between false positives and true positives. True positive detections trigger a predefined set of actions aimed at containing and eradicating the threat, followed by efforts to restore normal service. Complex cases that exceed standard remediation processes are escalated to senior incident responders for specialised intervention.
Microsoft Sentinel’s artificial intelligence hunts and investigates suspicious activities that could signal a breach. Its hunting capabilities help proactively detect potential issues before they cause damage. It allows organisations to understand how an incident or event occurred and how to stop it from happening again.
RESPOND : The artificial intelligence makes Azure Sentinel respond to the threat incidents and events rapidly. Proaxiom uses our own internally developed playbooks built on the foundation of Azure logic apps to respond to alerts. If an incident is discovered, built-in orchestration and automation goes to work to protect your environment.
HOW DO WE REPORT?
Clients receive monthly reports detailing the nature and volume of alerts processed, the sources of telemetry data, and the specific actions taken in response to detected threats. This comprehensive approach ensures clients are well-informed of the ongoing efforts to safeguard their environments against cyber threats.
HOW WOULD THIS MITIGATE A THREAT ACTOR LIKE A BLACKCAT ALPHV AFFILIATE?
Through our threat intelligence processes, Proaxiom knows that threat actors like Blackcat ALPHV affiliates, who vary in sophistication levels, use a standard set of Tactics, Techniques and Procedures that can be identified using the Mitre ATT&CK framework. For example, we know based on threat intelligence from the US Cybersecurity & Infrastructure Agency (CISA) that:

EXPLOITATION - DETECTION & RESPONSE
Actors pose as company IT and/or helpdesk staff and use phone calls or SMS messages [T1598] (Phishing for Information) to obtain credentials from employees to access the target network [T1586] (Compromise Accounts). We can detect T1586 (compromised accounts) through Microsoft Defender XDR and Sentinel logic – such as impossible travel and UEBA. We identify the compromised accounts, revoke their active sessions and reset the passwords before alerting the user and generating a post-incident report.
INSTALLATION - DETECTION & RESPONSE
After gaining access to a victim network, ALPHV Blackcat affiliates deploy remote access software such as AnyDesk, Mega sync, and Splashtop in preparation of data exfiltration. This constitutes the Mitre ATT&CK TTP called Use of Remote Services (T1021). We can detect this using custom SIEM logic that detects the use of these tools based on the telemetry from Microsoft Defender for Endpoint EDR. Because we have business context, we know that the target no longer uses these tools and we consider them malware. We isolate the affected device and remove the tools, conduct a forensic analysis of the machine to determine how the tools were installed. Then we eradicate the threat actor from the environment and generate a post-incident report.
ALPHV Blackcat affiliates create a user account, “aadmin,” and use Kerberos token generation for domain access [T1558]. We can detect this action through Microsoft Defender for Identity, a sensor that runs on domain controllers. We delete the user account, identify the source system that created the account using network logs, then we isolate and eradicate.


COMMAND & CONTROL - DETECTION & RESPONSE
After gaining access to networks, they use legitimate remote access and tunneling tools, such as Plink and Ngrok [S0508]. ALPHV Blackcat affiliates claim to use Brute Ratel C4 [S1063] and Cobalt Strike [S1054] as beacons to command and control servers. We detect these actions and tools using a combination of telemetry from Microsoft Defender for Endpoint for file hash IoCs, and network detection data derived from Zeek beacon detection and JA3 fingerprinting. We identify the source system and the destination URLs, IP addresses and domains. We isolate the source system, eradicate the C2 framework tools, and block the threat actor’s IoCs at the firewall and on Cloudflare WARP.
The list is long, and there are a lot of TTPs included in the report, these are just a small sample.
Finally, CISA provides a list of indicators of compromise (IoCs), including file hashes, IP addresses and domains that we use in Sentinel to match for threat actor activity in realtime.
