Threat Hunting
HOW IT WORKS.
Threat hunting is a proactive security practice where hunters search for indicators of compromise (IoCs) and TTPs within an organization’s environment that evaded existing security measures. By identifying and mitigating hidden threats before they can be exploited further, threat hunting disrupts the kill chain, preventing attackers from establishing a foothold or moving laterally within the network.

HOW PROAXIOM DOES IT
Proaxiom uses the industry standard TaHiTi model for threat hunting. It involves the following phases.
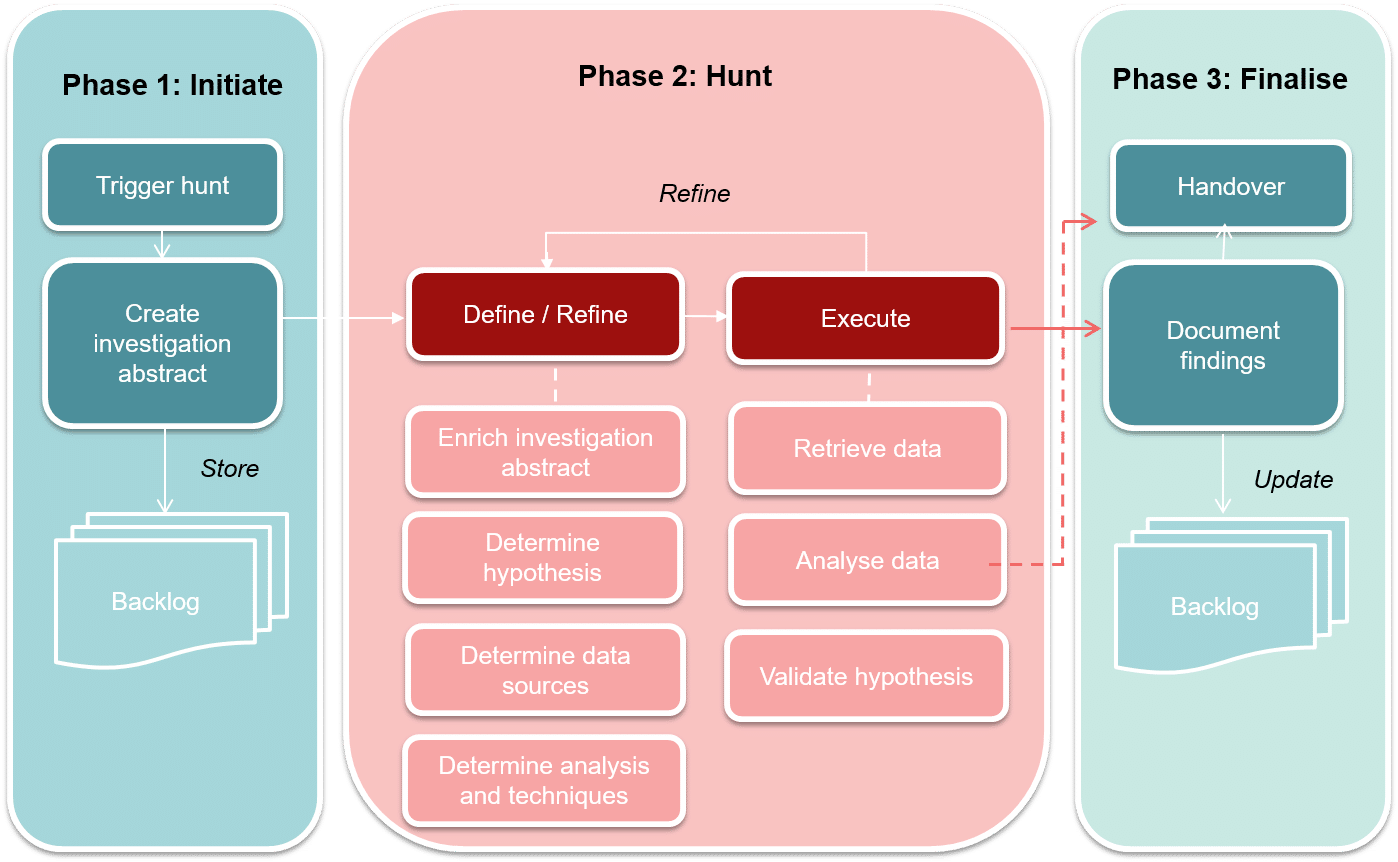
Initiate:
- The process begins with the trigger of a hunt, prompted by an indication of a potential threat.
- An investigation abstract is crafted, which outlines the goals and boundaries of the hunt. This document is critical as it incorporates custom threat intelligence to form hypotheses about possible threat activities. This intelligence is based on the understanding of adversaries’ behaviors and known attack vectors, making it a pivotal element in anticipating the moves of potential threat actors.
- The investigation abstract, enriched with threat intelligence, is stored in a backlog for organization and future reference.
Hunt:
- The hunt is informed by the initial abstract, which is continuously refined with ongoing analysis and intelligence.
- The process involves defining clear hypotheses, determining relevant data sources, and selecting appropriate analytical techniques to uncover potential threats. The hypotheses, crafted during the initiation phase, direct the focus of the hunt, ensuring efforts are not wasted on low-risk areas.
- Execution of the hunt includes data retrieval, in-depth analysis, and validation of the hypotheses.
Finalize:
- After executing the hunt, the team documents the findings in detail, which involves the nature of any threats detected, the data analysed, and the conclusions drawn from the hunt.
- The finalization phase culminates with a handover, where these findings are reported back to stakeholders. This phase is critical for providing transparency and ensuring that the results of the hunt lead to actionable insights.
- Updates, including insights and recommendations derived from the hunt, are added to the backlog to inform and enhance future threat hunting activities.
By integrating threat intelligence into the initiation phase, the hunting process is strategically aligned with the organization’s most pressing security concerns, ensuring that the hunt is both effective and efficient. The reporting process serves to close the loop, offering a thorough understanding of the threats and enabling stakeholders to make informed decisions to bolster security measures.
We initiate two separate planned proactive threat hunts per quarter, and will conduct reactive threat hunts in response to valid threat intelligence that indicates attacker activity that has a high likelihood of affecting the customer.
HOW DO WE REPORT?
We conduct two proactive threat hunts per customer, per quarter. We offer completed reports on the hunts, including the initiation, hunt and finalisation phases.
From time to time, we’ll also conduct reactive threat hunts in response to credible threat intelligence.
How would this mitigate a threat actor like a Blackcat ALPHV affiliate?
THREAT HUNTING CAN DISCOVER ASPECTS OF A THREAT ACTOR CAMPAIGN THAT WERE NOT DETECTED IN THE DETECTION AND RESPONSE PHASE BY INTRODUCING THREAT INTELLIGENCE.
If a sophisticated threat actor has managed to evade detection and response, but we receive credible threat intelligence that about their activities in other networks, we can detect them by hunting for their TTPs and IoCs in the Crest network environment.
In the event that we detect threat actor activity using this method, we initiate the incident response process and contain, eradicate, recover and report.
This can assist in detection across exploitation (using TTPs), installation (using IoC like file hashes) or command and control (using fingerprints like JA3).
